Introduction: What is a Firewall?
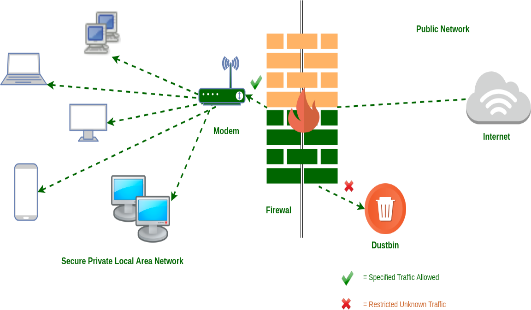
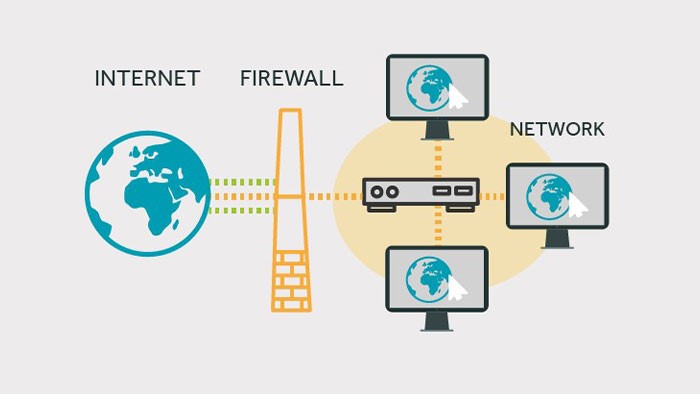
A firewall is like a bouncer at a club. It stands at the door and checks everyone who wants to come in. If someone doesn't have a valid ID, the bouncer doesn't let them in. Firewalls work the same way. They check all the traffic that comes into your network and make sure it's from a trusted source. If it's not, the firewall blocks it.
Firewalls are an important part of network security. They can help protect your data, systems, and network infrastructure from unauthorized access and potential cyberattacks. If you don't have a firewall, or if your firewall isn't configured properly, you're leaving your network vulnerable to attack.
What Firewalls Do?

Firewalls are like the gatekeepers of your network. They stand guard at the entrance, checking all incoming traffic to make sure it's safe. If something doesn't look right, they block it from entering.
Firewalls play a vital role in network security by performing three main functions:
Packet filtering:
Firewalls inspect packets of data based on specific criteria, such as source and destination IP addresses, port numbers, and protocols. They allow or block packets based on predefined rules, acting as the first line of defense against unauthorized network traffic.
Network Address Translation (NAT):
Firewalls with NAT capability modify network address information in packet headers, hiding internal IP addresses from external networks. This provides an additional layer of security by making it challenging for potential attackers to identify and target specific devices on the internal network.
Application Control:
Advanced firewalls can analyze network traffic at the application layer, allowing or blocking specific applications or services based on predefined rules. This helps organizations enforce security policies and mitigate risks associated with untrusted or potentially malicious applications.
Why Do We Need Firewalls?
Firewalls are essential for several reasons:
Network segmentation:
Firewalls enable organizations to divide their network into distinct segments, separating different departments, user groups, or sensitive systems. This isolation prevents unauthorized access and limits the impact of security breaches, creating additional barriers for attackers.
Imagine you have a big house with a lot of people living in it. You wouldn't want everyone to have access to all the rooms, so you put locks on the doors. Firewalls work the same way. They allow certain people access to certain parts of your network, and they keep everyone else out.
Protection against cyber threats:
Firewalls act as a frontline defense against various cyber threats, including unauthorized access attempts, malware infections, and Denial of Service (DoS) attacks. They inspect and filter network traffic, preventing malicious entities from compromising the network and compromising sensitive data.
Firewalls are like the first line of defense in a war. They stop the enemy from getting to your most valuable assets.Regulatory compliance:
Many industries have specific regulatory requirements regarding network security. Firewalls help organizations comply with these regulations by implementing access controls, encryption, and other security measures necessary to protect sensitive data.
Firewalls are like the law enforcement of your network. They make sure everyone is following the rules and that no one is doing anything illegal.
Security: Firewalls can help give you peace of mind knowing that your data is safe.
Confidence: Firewalls can help you feel confident in your ability to protect your business from cyber threats.
Relief: Firewalls can help you feel relieved knowing that you're taking steps to protect your network from attack.
Firewall Delivery Methods:
There are different ways to deploy firewalls, each with its own advantages and disadvantages.
1. Software firewalls:
Software firewallsare installed on individual devices, such as computers or servers, providing protection at the device level. They are cost-effective and allow users to customize security settings based on their specific needs.
Imagine you have a big house with a lot of people living in it. You wouldn't want everyone to have access to all the rooms, so you put locks on the doors. Software firewalls work the same way. They allow certain people access to certain parts of your network, and they keep everyone else out.
Software firewalls are a good option for personal or small-scale use. They are easy to install and configure, and they can be customized to meet your specific needs. However, they can be resource-intensive, and they may not provide the same level of protection as a hardware or cloud firewall.
2. Hardware firewalls:
Hardware firewallsare standalone devices placed between the internal network and the external network. They provide centralized security management and protect multiple devices simultaneously.
Hardware firewalls are a good option for businesses or organizations with a large network. They are more expensive than software firewalls, but they offer better performance and security. Hardware firewalls are also easier to manage and maintain than software firewalls.
3. Cloud firewalls:
Cloud firewalls are virtual firewalls provided by cloud service providers (CSPs). They are deployed in the cloud environment and protect cloud-based resources and networks.
Cloud firewalls are a good option for businesses or organizations that use cloud-based applications and services. They are scalable and flexible, and they can be easily integrated with cloud services and platforms. Cloud firewalls are also less expensive than hardware firewalls.
However, cloud firewalls are not without their disadvantages. They are dependent on the availability and reliability of the cloud service provider. They also offer less control over the underlying infrastructure. Additionally, there is potential latency due to traffic routing through the cloud provider's network.
Types of Firewalls:
There are several types of firewalls, each with its own strengths and weaknesses. Understanding these types can help businesses choose the most suitable firewall for their specific needs:
Type 1 - Packet-filtering firewalls
Packet-filtering firewalls can be implemented in hardware or software. Packet-filtering firewalls are simple and efficient, and they have a low impact on network performance. They are also easy to implement and configure. However, they have some limitations. They cannot inspect the contents of packets, so they are vulnerable to IP spoofing attacks. They also lack advanced security features, such as application control and intrusion prevention.
Despite their limitations, packet-filtering firewalls can be a valuable addition to any network security strategy. They can help to protect against a wide range of threats, and they are a relatively inexpensive way to improve network security.
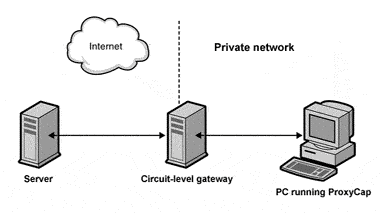
Type 2: Circuit-Level Gateways
Circuit-level gateways offer several advantages over other types of firewalls. They are transparent to external networks, meaning that they do not require any changes to be made to the network infrastructure. They also have minimal impact on network performance.
However, circuit-level gateways also have some limitations. They do not support advanced application-layer protocols, such as HTTP and HTTPS. They also cannot inspect packet contents beyond the transport layer, meaning that they cannot detect malicious traffic that is hidden within the payload of a TCP packet.
Circuit-level gateways are a good choice for organizations that need to improve security for TCP connections without making any changes to their network infrastructure. However, they are not a complete solution for network security and should be used in conjunction with other security measures, such as intrusion detection systems and application firewalls.
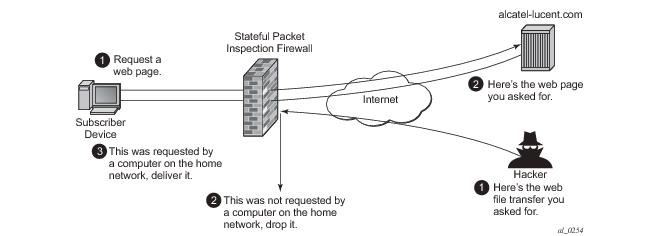
Type 3: Stateful Inspection Firewalls:
Stateful inspection firewalls offer several advantages over other types of firewalls. They can inspect packet contents, which allows them to detect malicious traffic that is hidden within the payload of a packet. They can also track connection state and context, which allows them to identify and block malicious traffic that is trying to exploit known vulnerabilities.
However, stateful inspection firewalls also have some limitations. They require more resources than packet-filtering firewalls, and they can introduce latency due to deep packet inspection. Additionally, advanced features of stateful inspection firewalls may require additional configuration and management.
Type 4: Proxy Firewalls (Application-Level Gateways/Cloud Firewalls)
Proxy firewalls offer several advantages over other types of firewalls. They can inspect application-layer traffic, which allows them to detect malicious traffic that is hidden within the payload of a packet. They can also provide enhanced privacy and anonymity, and they can add an additional layer of protection against application-level attacks.
However, proxy firewalls also have some limitations. They can introduce latency due to proxying traffic, and they may require specific client configuration. Additionally, they may not support certain protocols and applications.
Type 5: Next-Generation Firewalls (NGFWs)
NGFWs offer several advantages over traditional firewalls. They can inspect packet contents, which allows them to detect malicious traffic that is hidden within the payload of a packet. They can also track connection state and context, which allows them to identify and block malicious traffic that is trying to exploit known vulnerabilities. Additionally, NGFWs can provide advanced threat detection and prevention capabilities, such as malware detection and sandboxing.
However, NGFWs also have some limitations. They require more resources than traditional firewalls, and they can introduce latency due to deep packet inspection. Additionally, advanced features of NGFWs may require additional configuration and management.
Overall, NGFWs are a good choice for organizations that need to improve security for their networks. However, they are not a complete solution for network security and should be used in conjunction with other security measures, such as intrusion detection systems and application firewalls.
Which Firewall Architecture is Right for Your Company?
Choosing the right firewall architecture depends on several factors:
Size of the organization:
For small organizations or home networks, software firewalls may provide sufficient protection. Medium to large enterprises typically require hardware firewalls or a combination of hardware and software firewalls to accommodate their network size and complexity.
Availability of resources:
Consider the availability of technical expertise, budget, and infrastructure when selecting a firewall architecture. Hardware firewalls may require more resources and upfront investment, while software firewalls can be more cost-effective but demand individual device management.
Requirement of multi-level protection:
Organizations with advanced security needs may opt for next-generation firewalls or a combination of different firewall types to create a layered defense strategy. This approach allows for granular control and comprehensive protection against sophisticated threats.
Here are some additional factors to consider when choosing a firewall architecture:
The type of data you need to protect:
If you are storing sensitive data, such as credit card numbers or social security numbers, you will need a firewall that can provide strong security.
The type of network you have:
If you have a large network with many devices, you will need a firewall that can handle the traffic.
The budget you have:
Firewalls can range in price from a few hundred dollars to several thousand dollars.
What You Should Know Before Getting a Firewall
Before implementing a firewall, consider the following factors:
Network Architecture:
Understand your network topology, including the number of devices, their locations, and the traffic patterns. This information helps determine the placement and configuration of the firewall.
Security Policies:
Define the security policies and rules that align with your organization's requirements. Consider factors such as access control, application permissions, and user privileges.
Scalability and Future Growth:
Ensure the firewall solution can scale with your organization's growth. Consider future network expansion, new technologies, and emerging threats.
Management and Monitoring:
Evaluate the management capabilities and monitoring features of the firewall solution. Robust management tools and real-time monitoring help maintain and fine-tune the firewall's effectiveness.
Why Choose Al Hutaib for Firewall Solutions in Dubai:
Here are some reasons why you should choose Al Hutaib for your firewall needs in Dubai:
Expertise:
Al Hutaib has been providing IT solutions in Dubai for over 20 years. They have a team of experienced and certified engineers who can help you choose the right firewall for your needs and implement it correctly.
Reliability: Al Hutaib is a reliable and trustworthy company. They have a proven track record of providing quality IT solutions to their customers.
Competitive pricing: Al Hutaib offers competitive pricing on firewall solutions. They can help you find the right firewall for your budget.
After-sales support: Al Hutaib offers comprehensive after-sales support for their firewall solutions. They have a team of engineers who are available 24/7 to help you with any problems you may encounter.
If you are looking for a reliable and trustworthy company to provide you with firewall solutions in Dubai, then you should consider Al Hutaib. They have the expertise, reliability, competitive pricing, and after-sales support that you need to protect your network from attack.
Here are some of the firewall solutions offered by Al Hutaib:
Cisco ASA Firewalls:
Cisco ASA firewalls are a popular choice for businesses of all sizes. They offer a wide range of features and are easy to manage.
Juniper SRX Firewalls: Juniper SRX firewalls are another popular choice for businesses of all sizes. They offer a wide range of features and are known for their reliability.
Fortinet Firewalls: These firewalls are a good choice for businesses that need advanced security features. They offer features such as intrusion prevention, application control, and data loss prevention.
Al Hutaib can help you choose the right firewall for your needs and implement it correctly. They also offer comprehensive after-sales support to help you with any problems you may encounter.
FAQs
1. What are the different types of firewall security?• Packet-Filtering Firewalls
• Circuit-Level Gateways
• Stateful Inspection Firewalls
• Proxy Firewalls (Application-Level Gateways/Cloud Firewalls)
• Next-Generation Firewalls
2. What are the 3 methods of firewall?
• Packet Filtering
• Circuit-Level Gateways
• Stateful Inspection
3. What is the most basic firewall?
The most basic firewall is a packet-filtering firewall.
4. How do firewalls work?
Firewalls work by monitoring and controlling network traffic based on predefined security rules and policies. They examine packets of data and allow or block them based on specific criteria.
5. What are firewall rules?
Firewall rules are predefined instructions that dictate how a firewall should handle incoming and outgoing network traffic. These rules determine which packets are allowed or denied based on various criteria.
6. What is a proxy firewall?
A proxy firewall acts as an intermediary between client devices and external networks. It receives, evaluates, and forwards network requests on behalf of the client, providing an additional layer of security.
7. Can a firewall block an IP address?
Yes, a firewall can block specific IP addresses or ranges by defining rules that deny traffic from those sources. This helps prevent unauthorized access or malicious activity from those IP addresses.
8. Where are firewalls required?
Firewalls are required in any network environment where security is a concern. This includes businesses, organizations, educational institutions, government agencies, and even individual home networks.
Related Services by Al Hutaib
Structured cabling system in DubaiAccess Control System in Dubai
Data Center in Dubai
Cloud Backup & Data Recovery
Network Maintenance contracts (Remote and On-Site)
Recent Blogs
How Network Solutions in Dubai Drive Business Growth and ProductivityTop 5 Benefits of Using Cloud Computing for Small Business
How Can a Blockchain be Used in Business? A Comprehensive Guide
Developing A Website? Do You Know The Rules For Success
How To Maintain Computer Systems In Your Company?
Mobile And Web Development – Highest Demanding Services In UAE
Choose the Right CCTV Camera Installation System in Dubai
Best HRMS Software in Dubai